Hidden Proxy in 2026 – Important Things You Need to Know
When you think about a hidden proxy, the next thing that comes to mind will likely be online phishing. Yes, most of the time, hidden proxy servers act as the gateway to accessing people’s information, such as their website address, website activity, and credit card information. But it does have legal use as well. In
When you think about a hidden proxy, the next thing that comes to mind will likely be online phishing. Yes, most of the time, hidden proxy servers act as the gateway to accessing people’s information, such as their website address, website activity, and credit card information. But it does have legal use as well. In the upcoming sections, we will see about proxy servers and what a hidden proxy is and explore its impacts.
Feel free to jump to any section to learn more about hidden proxy!
How Are Hidden Proxies Used as a Medium to Hack People?
How to Delete Hidden Proxy Servers?
A Proxy Server – What Is it?
A proxy server is an intermediary server that sits between you (the client) and the target server (the online server). Usually, when you connect your devices online, you request access to the information sent to the target server directly with the help of your IP address. Your IP address provided by your ISP (Internet Service Provider) is tied to your physical location, meaning that when you request access to the target server, based on your IP address information, the target server gives you access.
So, what if you are trying to access data that is not available in your region? The target server will reject your request for access to that data, and based on the number of requests that you send (if you are using any bots to perform a specific task) then, you may get an “IP block” from the target server.
You can avoid such scenarios by using a reliable proxy server. Not only for filtering contents online but also for using proxy servers to access restricted content unavailable in your region. Then, your connection would be a three-way connection instead of the generic two-way communication. This also allows you to hide your IP address since proxy servers’ IP addresses mask your original IP address.
The probability of getting banned online can be considerably reduced.
A Hidden Proxy Server:
A hidden proxy server is a server system for filtering user internet traffic that is not visible to the user. A hidden proxy is mainly used to set up a hidden server with a fake website as the front. This is a big help when filtering out other proxies that try to access your servers. This approach makes it challenging for cyber hackers to access your actual website and its information, such as the user’s website activity and payment details. To know more about the recent cyber attacks, refer this link
How Are Hidden Proxies Used as a Medium to Hack People?
Hidden proxy is a term used many times in phishing. Even though it is beneficial in securing your information from cyberattacks, most people have already made up their minds about hidden proxies as an illegal approach to gathering sensitive information. The primary method of getting information is in the form of sending emails. These are considered spam emails. Hackers send these spam emails to users, unaware that when they click on them a hidden proxy runs through their computer as a background task.
The critical thing to understand is that these emails are represented as emails from the Internet service provider (ISP). In this way, users open the email believing that it is from ISP. The email follows usual patterns, such as asking you to click on a suspicious link and asking you for access, such as your username and password to your internet connection. The other approach is falsely accusing the user.
The process starts with the hacker sending an email to impersonate an ISP. The hackers send spam emails to unaware users and ask them to follow some procedures to get their personal information, such as social security numbers, payment information, and much more; otherwise, the falsely accused user account will get suspended or deleted.
Once the user clicks on the suspicious link, the malicious software installs on the user’s computer. In this way, whenever a user connects to a network, the hacker can trace the web activity and extract the payment and personal information of the user. The malicious software crawls through all the data and regularly sends it to the hacker in a secure tunnel.
The other aspect of hidden proxies are students and office personnel accessing their respective work networks by bypassing the web filters. Avoiding web filters is simple since there is already a proxy server running in the school or work computer. This proxy server acts as the course for accessing a local website. This is commonly known as “proxy avoidance.” You can overcome proxy avoidance by setting up a series of web filters within the proxy servers.
How to Delete Hidden Proxy Servers?
Most of the time, hidden proxies are configured by the network setting in the computer. You can carry out these exact steps regardless of the default browser.
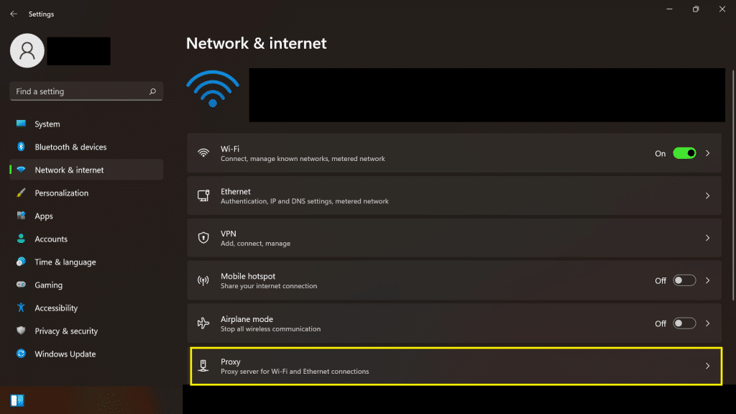
STEP 1: Click “Start”–> Select Control Panel. You can see the list of settings; from there, you can identify the Network option.
STEP 2: Select “Network & Internet connection.” You should be able to see the option “Proxy server.” Select that option.
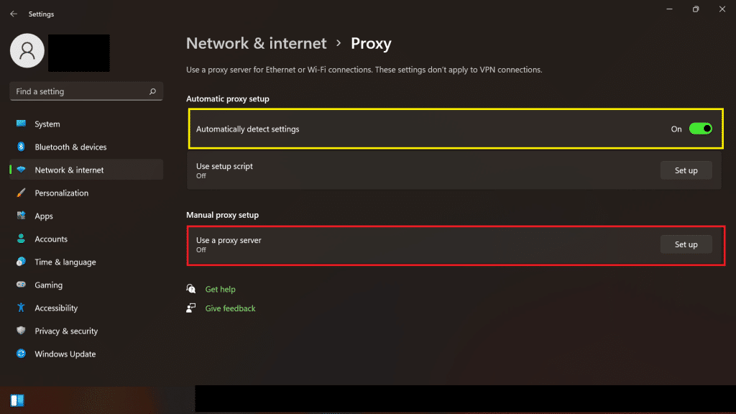
STEP 3: Now, the last step is to deselect the option “Automatic detect setting” and make sure “Use a proxy server” is OFF.
FAQs:
FAQs:
1. What does a proxy hide?
2. What is the best proxy for hiding your IP address?
3. Do proxies encrypt your website activity?
4. How does the proxy hide your IP address?
Conclusion:
The hidden proxy looks like a bad thing in the internet sector, but there are advantages also. You can use a hidden proxy as a false front for your work and ensure that there is a reinforcement to your security. The proxy does have some disadvantages, such as no encryption to internet traffic, and the internet connection sometimes lags or stutters. But, at the same time, the proxy gets the job done compared to its counterparts, such as a VPN, and at a considerably low price.
ProxyScrape offers premium servers for various internet activities and free stuff, such as web proxies, APIs, and proxy filters. With 7 million pools, you can rest assured that all the proxies will be constantly online. You can be assured that almost 100,000 proxies will be available at any point in time.
DISCLAIMER: This article aims to create awareness about the remote proxy and its good and bad benefits. This article does not support any hidden proxy scam. This post is only for learning purposes.