How Reverse Proxies Enhances your Web Application’s Security

It’s no secret that businesses are increasingly using web applications in this day and age. Web applications make it convenient to streamline corporate operations, enhance efficiency, and thus save expenses for tasks that would otherwise be done manually. Web apps are prone to risks and cyberattacks despite their growing popularity. This article will provide insight
It’s no secret that businesses are increasingly using web applications in this day and age. Web applications make it convenient to streamline corporate operations, enhance efficiency, and thus save expenses for tasks that would otherwise be done manually.
Web apps are prone to risks and cyberattacks despite their growing popularity. This article will provide insight into the significant attacks that a web application is vulnerable to. Then you’ll discover how you can incorporate a reverse proxy to minimize the threats.
But before diving into security aspects, let’s take a look at the architecture of a typical web application.
Overview of web application architecture
Web Application
In most circumstances, web applications consist of web servers and web pages. Web servers accept requests from clients(your web browsers), which a web server process and returns the response to the client.
While the server-side is coded using dynamic programming languages such as PHP, Python, ASP.NET, etc., the client-side is coded using HTML, CSS, and JavaScript.The communication between the client and server takes place through HTTP protocol.
You may refer to this article for further information about the structure of web applications. The below figure shows a typical client-server communication.
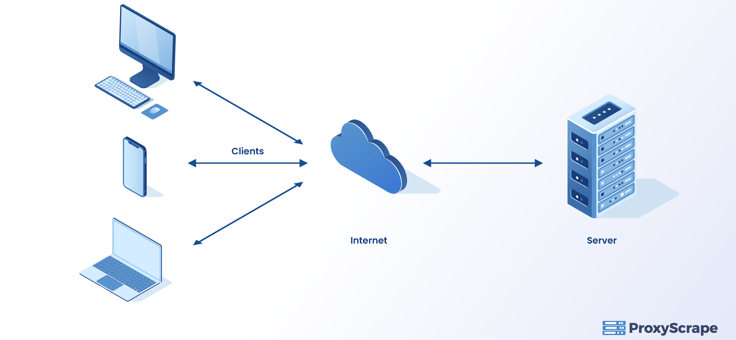
All communication appears to be straightforward in the diagram above, with requests traveling back and forth between the client and the server. However, this is not always the case.
Unfortunately, web applications using the above design are subject to cyberattacks by outsiders between the client and the server.
Let’s take a look at some of the most exciting cyber attack statistics before we dive into the nature of these attacks.
What are the significant threats to a Web Application?
Exciting stats about cyberattacks
According to Positive Technologies’ web application vulnerabilities data from 2018, the Finance and Banking industries accounted for 28% of all attacked web applications. It also indicates that 14 % of the cyberattacks target online applications in the Telecom and Manufacturing industries, with 11 % targeting transportation applications.
Other industries that face risks include government institutions (11%), IT, E-commerce, and the mass media.
As far as the types of attacks are concerned, another report, F5, states that cross-site scripting(from 4% to 54%) and SQL injection (SQLi) attacks (from 15% to 76%) are rising.
We can arrive at a conclusion from these statistics that some stringent measures are required to protect web applications from vulnerabilities. Some of the security flaws occur due to the issues in coding, whereas other reasons could be due to inadequate infrastructure used by the web application. This is where the Web Application Firewall (WAF) comes into the picture which can minimize vulnerabilities by filtering packets, blocking HTTP traffic, and unauthorized logging.
We will explore it further below. Before that, a brief overview of significant security threats.
SQL injection (SQLi)
SQLi -SQL injection is a web security vulnerability that lets the attacker manipulate SQL queries that an application makes to the database. By doing so, they gain access to potentially valuable information that anyone can not reach easily.
A simple, most familiar example would be to take advantage of unsanitized user input to the hacker’s advantage. Let’s assume that there is a text box that requests user ID. Then based on the User ID, the query retrieves all the information belonging to that user.
So suppose in the text box if the user had entered the below:
User Id: 228 or 1=1
Then the resulting query would be the below:
SELECT * FROM Users WHERE UserId = 228 OR 1=1;Then it would retrieve all the data in the user’s table, including passwords if the table contains password data.
For further information about SQLi, you may refer here.
Cross-Site Scripting (XSS)
XSS occurs when a user injects a malicious script mainly in javascript through unsanitized input fields. Usually, an attacker sends this malicious script to a user who will not be suspected. The end user’s browser is unaware that this script is harmful and will execute the script.
As a result, this malicious script can access all the data associated with cookies, session tokens, or any other sensitive information. Furthermore, these scripts can rewrite the HTML of a webpage.
Broken authentication and session management
Suppose a user would have to log in to a web application using the login credentials. In that case, the website’s proprietary algorithm generates a unique session ID for the entire communication between the user and the webserver for that session.
If the web developers have not encrypted secure data that travels back and forth between the user and the webserver, there are high chances for an intruder to steal it and act as the user. This scenario mainly occurs when you log into the internet using public WiFi in coffee shops.
You may refer to this article for further details.
What are the methods to prevent web attacks?
Web Application Firewall
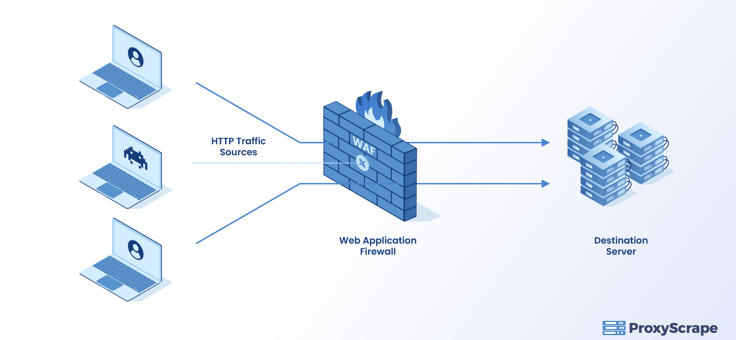
WAF is a layer 7 defense in the OSI model which can be placed at the entry point to the destination server, as shown in the below diagram. It protects the server’s internal network from attacks and hides the network topology of the server.
In order for WAF to work, you should make additional configurations in the server. Like the firewalls, WAF filters incoming and outgoing HTTP traffic that appears dangerous to the server’s internal network if they don’t satisfy the rules that you set on the WAF.
WAF is also a type of reverse proxy that we will discuss in the next section.
Reverse Proxy
A job of a proxy server is to hide your IP address and replace it with that of the proxy server. Well, a reverse proxy also does the same and enhances the web server’s security by hiding it as well as the internal network topology of the server.
The client only knows the proxy server’s address, and hence the actual server is hidden from the client.
Ideally, you can use a reverse proxy as a Web Application Firewall (WAF) which we discussed above. You can implement WAF on web applications on devices with reverse proxy configured. As a result, the scope of WAF in enhancing security becomes wider. The attacker is also unable to see the actual location of the webserver.
You may refer to this article for further fundamental information about reverse proxies. In the next section, we shall look into using a reverse proxy to mitigate the application risks. However, before that, let’s provide you with an overview of what a reverse proxy does.
How does reverse proxy work?
All reverse proxies perform all the following fundamental operations:
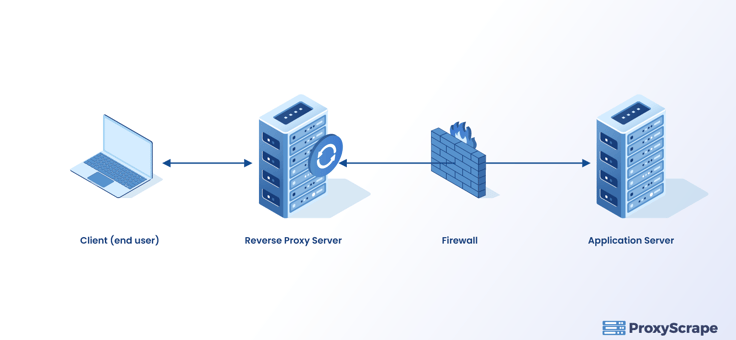
- The client browser sends an HTTP request to a public URL. Let’s assume the URL to be www.host.com on port 80.
- Then, as usual, the hostname resolves around the reverse proxy server. This reverse proxy server listens to this address and receives the request.
- After that, the reverse proxy investigates the URL to determine where it needs to proxy the request. Usually, a reverse proxy may use any URL component to decide where to route the request. For example, it may use host, protocol, path, port, or query string. Usually, the path is the main component that decides routing.
- The Reverse proxy configuration settings determine the outbound URL to send the request to. This outbound URL is usually the back-end server responsible for providing the contents. The reverse proxy server may rewrite the parts of the request. It might, for example, alter or add to route segments.
- Then the next step is the request header revamping; The reverse proxy must also update some of the HTTP header information to indicate the internal web server in addition to remapping the URL. The “Host:” header, for example, contains the hostname from which the URL is requested.
- So to conclude the URL mapping,http://www.host.com could be remapped to http://realhost.com:8080.As, you can see in this case the hostname changed to realhost. Then the port number also changed to 8080.
- Finally, the reverse proxy sends the request to the actual server, which processes the request.
- After the server processes the request, it sends the response to the reverse proxy.
- Then the reverse proxy does the following:
- It modifies the response for it to send to the client correctly. This includes the “Location:” field, which contains the file’s server location.
- Reverse proxy remaps the headers and finally sends the response to the client.
How to secure your web application with reverse proxy
Since our objective is to overcome the cyberattacks mentioned previously, the reverse proxy needs to perform additional functionalities besides the steps mentioned above.
Validating the content of the request
When a client sends a request to the server, the reverse proxy will sanitize the input by comparing it with its signature database. The programmers develop these signatures with highly advanced regular expressions. The Reverse proxy’s decision to allow the request with the user input will be solely based on the blocklist filter and whitelist filter approach.
Blacklist filter approach
The blacklist filter stores the known harmful requests. It then compares each request to the entries in the list. If it discovers a match, it rejects the request. Different variations of the same assault must be recorded separately in the list. You would be able to prevent only the known assaults using blacklists.The black list’s comprehensiveness helps to its efficacy.
Whitelist filter approach
A whitelist filter captures the entire collection of valid requests for a specific site. As a result, the white list prevents attacks by only allowing known requests to reach the server. The process of constructing a white list, on the other hand, is time-consuming and requires knowledge of the whole range of legitimate requests that a user can potentially send to a server.
Furthermore, it can be overwhelming to create all the valid requests to hundreds of thousands of database vendors out there in case of SQL injection
Any modifications to a secured web application would necessitate a whitelist update. As a result, keeping a whitelist adds to the administrative burden.
Validating the content of the response
Before sending the response from the server back to the client, the reverse proxy validates it. A blacklist is used to accomplish this usually. The blacklist filter may hide known responses from clients who don’t need to view them. Error messages are an example of this type of data; the reverse proxy can replace the error with a generic error message containing no sensitive data.
Logging of request and response
The reverse proxy can also log the request for subsequent examination. The best approach is to configure logging for only the requests that reverse proxy blocked initially. You should carefully examine the logs throughout the first stages of installation. This is essential to verify that the reverse proxy does not block any genuine requests.
Conclusion
In this article, we hope you understand the vulnerabilities in a web application and how you can use a reverse proxy to resolve these threats. Indeed, the reverse proxy will not evict all the possible vulnerabilities associated with web applications.
However, it would be a great strategy to mitigate most of the threats you encounter in a web application. So finally, we hope you will apply the concepts learned in this article should you experience security concerns in your web application.