It’s important to secure your network because it is vulnerable to external threats and attacks. An attack on a single system can bring the whole network down and compromise the confidential information of an organization. Personal computers, businesses, and governments must secure their network to safeguard them from viruses, unauthorized access, and other threats. This
It’s important to secure your network because it is vulnerable to external threats and attacks. An attack on a single system can bring the whole network down and compromise the confidential information of an organization.
Personal computers, businesses, and governments must secure their network to safeguard them from viruses, unauthorized access, and other threats. This requires users to implement hardware devices like routers and firewalls, and software like antivirus and malware removal to protect their networks.
Users utilize proxies in a network to provide security, anonymity, load balancing, and speed. The main purpose of proxies is to provide security by hiding your internal network from the internet.
A firewall prevents unauthorized access to your computer by blocking ports and programs. While a proxy and firewall serve the same purpose of providing security, they differ in their purpose and their work.
What is a Proxy?
Proxies act as a gateway or an intermediary between any device and the rest of the internet. Users implement them at the server-side, which is why it is also called a proxy server, but there are client-side proxies also that do the same job as a server-side proxy.
A proxy accepts, forwards, and returns data for requests. It uses the anonymous network ID instead of the original IP address, which hides the IP address of the client.
Proxy servers are often known as the application gateway, as it manages traffic at the application level. Proxy server filters data based on header fields, message size, and content.
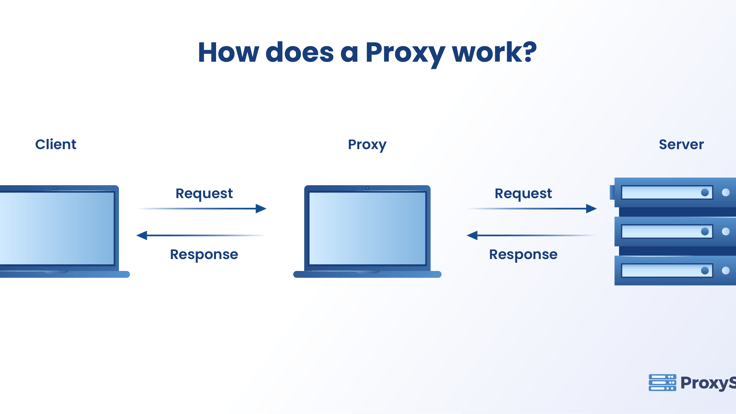
How Does a Proxy Work?
Proxies provide more control over what comes in and goes out of a network. The proxies are categorized as web proxies or server-side proxies.
The request from the user first goes to the proxy server which forwards this request to the actual server, collects the response, and forwards it to the user. Proxy servers can make changes to the data the user sends and still get the requested information.
Proxies change the IP address, so the server can’t know the user’s actual IP address. It also encrypts the data, so that it couldn’t be read by intruders or malicious users and proxy servers block certain users based on their IP addresses.
Proxy Cache
A proxy receives a request from a client and accesses the server to process the request. First, it searches for that same request in the cache, and cached requests consume fewer connection speeds due to a faster delivery speed. Otherwise, the proxy obtains the response from the web directly.
When a user wants to access a website on the internet the request gets forwarded to a proxy server, which searches in the cache and looks for that request. If the request is available, the proxy gives the reply to the user.
If the user-requested data is not found in the cache, then the proxy forwards it to the server. The response from the server is given back to the client and cached at the proxy.
What is a Firewall?
A firewall is a software or application that protects a local network by blocking access to unauthorized users. It works at the IP layer of the TCP/IP protocol model and filters data packets entering a private network. A data packet can enter the network only if the firewall allows it. It is a fool-proof method for monitoring, protecting, and auditing the local network from external security threats.
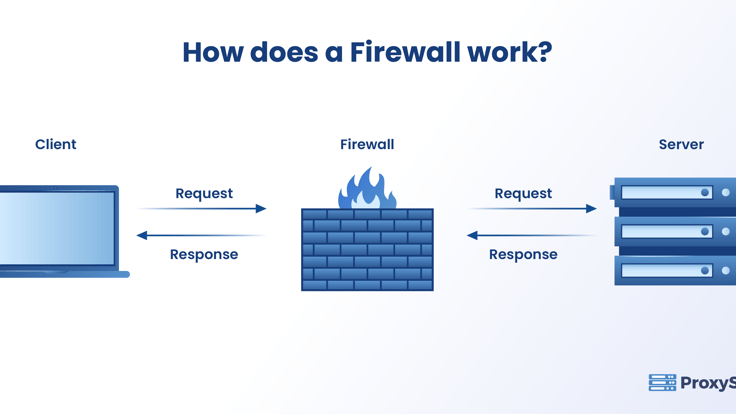
How Does a Firewall Work?
A firewall protects the network, devices attached to the network, and its data by managing the network traffic. The network administrator governs the traffic to ensure security in a private network.
A firewall establishes a boundary between the external network and the home network it guards. It inspects the data that enters and leaves the home network based on the information maintained in the Access Control List (ACL). The ACL ensures to allow only the trusted sources that are IP addresses saved in the ACLs to enter the network.
A firewall can:
- Limit the Trojan horse from damaging your computer.
- Stop hackers from entering your network.
Access Control List (ACL)
ACLs are network traffic filters that control incoming and outgoing traffic. It works on user-defined rules to either forward or block a packet at the router’s interface. The ACL restricts, blocks, or allows packets that flow from the client, or source, to the server, or destination.
When users implement the ACL at the routing device, all the traffic flowing through it will be compared with the ACL rules defined there. Based on the rules, the ACL will either block or allow the data.
The criteria for defining the ACL’s rules could be based on the source’s specifications about what data should enter the network. It compares the IP address in the blocked lists that contains the IP addresses of malicious users or websites that tried to cause damage previously.
Users can configure ACLs in any device in the network, client system, or on the server.
Proxy vs Firewall – 10 Key Differences
| Feature | Proxy | Firewall |
|---|---|---|
| Purpose | Let you access the internet anonymously. | Protects the internal computers from threats. |
| Function | Directs the request of the client to the server. | Protects the network from attacks. |
| Location | It is an intermediate system between the user and the server to retrieve the data. | It functions on the perimeter of your organization or your home. |
| Resides on | Reside on both sides of the public network. | Between private and public networks. |
| Filtering | Filters and discards the data arriving from the banned websites. | Allows traffic to pass through the network and blocks only if the data is from a user that is in the ACL. |
| Implementation | The proxy server is implemented on the application layer of the TCP/IP stack. | The firewall is implemented at the network and transport layer. |
| Overhead | The overhead is less because it makes use of a cache from where it can fetch the request. | Having a firewall will generate more overhead as it authorizes whether a particular request can enter the network or not |
| Traffic | When you use a proxy server in your network, the traffic flows through the proxy server and comes back through the same proxy. | When a firewall is used, it provides security by filtering incoming and outgoing traffic based on a set of user-defined rules. |
| Rules | Proxies make use of a cache that stores the content. When a request comes from the client, the proxy verifies in the cache first before forwarding it to the server.The proxy server coordinates with the actual server to cache documents such as files, images, and web pages. | Firewalls make use of Access Control Lists (ACL) that are a collection of permit and deny conditions called the rules.The firewall checks the ACL before allowing or blocking the requests. |
| Unauthorized user | The proxy server redirects the unauthorized user to a different web page. | The firewall blocks unauthorized access. |
Closing Thoughts
It is imperative to maintain network security every second because a massive amount of data is transferred between computers and other devices. When you secure your network, the users and the devices connected to it work without any data breaches.
There are many proxy providers on the internet and ProxyScrape provides you with many options including providing unlimited bandwidth and connections. You can visit the site to know more about the services they provide and also compare with other providers.
Sometimes software and apps on your computer can abuse their permissions to create unauthorized network connections, but a good firewall on your PC has to request permission before it connects online. There are firewall solutions online that you can make use of to have a safe user experience on the internet, and it’s best to get one as soon as you can.