
Everyone is concerned about their privacy. According to purplesec, cybercrime skyrocketed to 600% during the COVID pandemic. These malicious actors leverage the user’s network vulnerabilities to perform these unethical activities. People want to browse online anonymously to secure their personal and sensitive information. The other reason to be anonymous online is to access geo-restricted content
Everyone is concerned about their privacy. According to purplesec, cybercrime skyrocketed to 600% during the COVID pandemic. These malicious actors leverage the user’s network vulnerabilities to perform these unethical activities. People want to browse online anonymously to secure their personal and sensitive information. The other reason to be anonymous online is to access geo-restricted content and bypass the web filters to access the restricted networks.
There is an option that is popular right now, which is VPN. VPN is good when it comes to security and such, but the drawbacks, such as low internet speed, the installation of client VPN software, and having to set up a VPN server, as well as subscribing to VPN service outweigh the advantages. This is not a viable option for some people. So, what is the solution to these issues? Well, the simple option is to use the SSH SOCKS proxy.
In the upcoming section, we will learn more about the SSH SOCKS proxy.
Table of Contents
- What Is an SSH SOCKS Proxy?
- What Is the SOCKS Proxy Protocol?
- How to Setup an SSH SOCKS Proxy Tunnel in Windows?
- SSH SOCKS Proxy For ProxyScrape
- FAQs:
- Conclusion:
What Is an SSH SOCKS Proxy?
SOCKS proxies and SSH (Secure Shell) are actually two different things. The SOCKS proxy is a proxy, where SSH is a protocol or technically a software package that imposes the secure system administration and data transfer over the insecure network.
What Is the SSH Protocol?
The SSH protocol helps to encrypt the network connection between the client and the target server. The main aim of the SSH protocol is to prevent any form of cyberattack on the network. The SSH protocol encrypts all forms of traffic, such as user authentication in the payment gateway, file transfer from the cloud storage, and programming outputs for sensitive problems.
Uses of SSH Protocol:
The SSH protocol is mainly implemented in corporate networks. The reason for implementing the SSH protocol in a corporate environment is:
- To manage critical projects and experiments by having an encrypted network environment.
- Seamlessly transfer a large amount of data over the encrypted network and sometimes automate the whole file transfer process.
- Provision of sensitive programming commands remotely over the network.
To implement the above three processes, the client needs secured access. The SSH protocol helps to provide secure access to the client and automate the process without human monitoring.
How Does the SSH Protocol Work?
As mentioned above, the SSH protocol helps to encrypt the network connection between the client and the target server. The four steps involved in the workings of the SSH protocol are as follows:
STEP 1: For any kind of client-server connection, the first step is to establish a connection between the client and server. The same thing is for the SSH protocol, the first step is to establish a connection between the SSH client and the SSH server.
STEP 2: Once the connection is established, the next step is to identify the SSH server. You can do this when the SSH server sends the public key to the SSH client.
STEP 3: Once the setup is completed, both the SSH client and server negotiate the parameters and the client asks the server to open the connection on a secure channel.
STEP 4: The SSH protocol helps to establish the encrypted network using strong hashing algorithms (Standard Hash Algorithm – SHA-2). Lastly, users can log into their server host operating system
Now you know what a SSH protocol is and how it works. Next, we will discuss the SOCKS proxy.
What Is the SOCKS Proxy Protocol?
SOCKS – Socket Secure is a protocol that imposes communication by redirecting internet traffic to the targeted server on behalf of the client through the client’s firewall. The normal IP address does not allow the user to bypass the firewall to access the restricted server. But the SOCKS proxy server helps to create a TCP (Transmission Control Protocol), which is used to communicate with a targeted server behind the client’s firewall. In simple words, SOCKS proxies relay only the TCP and the UDP (User Datagram Protocol) to the targeted server.
The main restriction with SOCKS proxies is, since the SOCKS proxy is based on layer 5, it does not apply to the tunneling protocol below layer 5. SOCKS can accept request types, such as HTTP, HTTP3, and FTP.
The SOCKS4 Proxy vs. The SOCKS5 Proxy:
So, it is well known and recommended that SOCKS5 is better and more secure when combined with SSH tunneling to encrypt network traffic. Since SOCKS5 has several authentications, SOCKS4 lacks authentication. Another main difference is that SOCKS4 does not support UDP, which means that users can only send small packets of data and that too moves at a slower rate. SOCKS5, on the other hand, does support UDP, which has the capabilities to send clusters of data at a faster rate. NOTE: SOCKS5 is faster than VPN and easy to use because SOCKS5 does not require any special software setup.
Now that you have a basic idea about SOCKS5 proxies and how it is better than SOCKS4 proxies, let’s see how to connect to the SSH server using a SOCKS proxy. NOTE: The upcoming steps can also be used for HTTP/s proxies and is applicable only for WINDOWS users.
How to Setup an SSH SOCKS Proxy Tunnel in Windows?
The main objective of this setup is to securely re-route your network traffic from your local system. NOTE: You can choose your port number as long as it is any number greater than 1024. Ports greater than 1024 are called privileged ports.
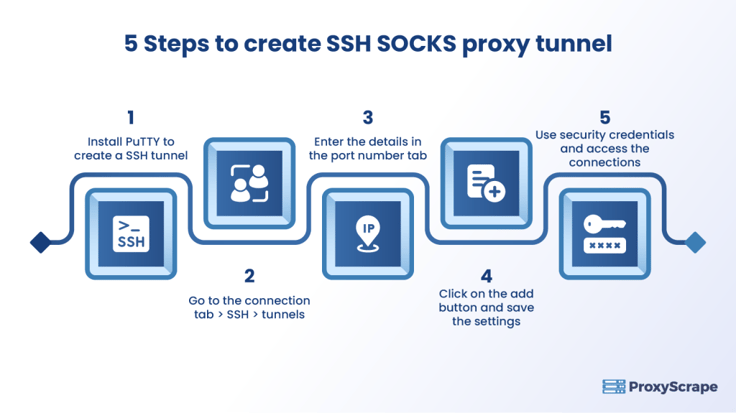
STEP 1: Choose port number “9090,” since “9090” is generally considered for this process. The server port is “20.”
[FOR WINDOWS]
STEP 2: Install PuTTY. Once you download PuTTY, enter the SOCKS5 proxy server IP address in the host IP address field. You can get your SOCKS5 proxy from ProxyScrape. All SOCKS5 proxies are based on SSL technology, so you can rest assured that your network activity cannot be tracked by the targeted source.
STEP 3: Go to the connection tab →SSH →Tunnels. Now click on the source port number tab and enter “9090.” NOTE: Use the port number as the same as the number used in the previous step. Do not forget to check the “Dynamic” radio box. Once you enter the port number, click the Add button to save the settings.
STEP 4: Once you add the button in the settings, it is recommended that you save the settings so you do not need to enter the proxy details again. Click on the “Session” tab and navigate to the “Saved” section. Give any name you want and save the settings.
STEP 5: To access the server, click on the “Open” button and you will see new windows asking for security credentials, such as your username and password. Once you enter your credentials, you will establish a connection to the secure SSH tunnel.
Now you can configure your default browser to the SSH SOCKS proxy. For Google Chrome, since it uses default settings for the proxy, it is better to use add-ons or extensions from the Google Chrome store. This will save time and you’ll have no need for any programming knowledge. You can install add-ons such as FoxyProxy, ProxMate, and SwitchyOmega. Add the extension and it will detect the SSH SOCKS proxy and connect to a secure SSH tunnel.
Now you know how to connect to a secure SSH server by using a SOCKS proxy.
SSH SOCKS Proxy For ProxyScrape
High Bandwidth – Socks 5 proxies of Proxyscrape will help users of high bandwidth which supports users to handle high-dimensional data from multiple sources.
Uptime – Proxyscrape functions 24/7 which assures uninterrupted functionalities. So, these socks proxies will be the best option for users to scrape unlimitedly.
Multiple Types – Proxyscrape provides proxies of various types. They furnish proxies of all protocols like HTTP, socks4, and socks5. They also provide residential proxies, dedicated proxies, and data center proxies.
Global Proxy – Users can make use of socks proxies of their desired location. They offer proxies from more than 120 countries.
Cost-Efficient – The premium proxies of ProxyScrape are of affordable cost and high bandwidth. Check out our attractive prices and huge proxy options.
FAQs:
1. What is an SSH SOCKS proxy?
2. What protocol does a SOCKS5 proxy use?
3. How do I install the SSH SOCKS proxy tunnel?
Conclusion:
The SOCKS proxy with SSH tunneling is the best alternative for VPN. The first installation takes time, but in the long run, it will be much faster than a VPN. The thing is, you can just authenticate without entering the username and password By getting a “public-key” authentication, the connection will be authenticated automatically. There are other functions such as SSH forwarding, and opening backdoors to the enterprise network, but those approaches also come with a cost, opening a backdoor prone to getting attacked by malicious actors and hackers. But for safe internet surfing and protecting your sensitive information, an SSH SOCKS proxy is the way to go!