What is a Subnet Mask?
In a network, every host and router has a unique IP address that encodes its network number and the host number. This IP address serves as an identification on the network to forward the data packets to the right computer on the network. The IP addresses are 32 bits long and present in the source
In a network, every host and router has a unique IP address that encodes its network number and the host number. This IP address serves as an identification on the network to forward the data packets to the right computer on the network.
The IP addresses are 32 bits long and present in the source and destination address fields of the request and response packets. The 32 bits of the IP address are grouped into bits of 8, making 4 bytes and part of the IP address identifies the network to which it belongs.
Either the first, second, third, or all of three bytes represent a subnet address and the remaining represent the address unique to the computer.
Class B subnetwork
Classification of IP addresses
The communication on the internet follows the TCP/IP protocol suite, which is a set of protocols with two versions, version 4 and version 6. The IPV4 is a 32-bit address whereas an IPV6 is a 128-bit address. An IPV4 uses numeric values, and IPV6 uses hexadecimal values.
The internet classifies the IP addresses into five categories or five classes known as the classful addressing. It is classified as class A, class B, class C, class D, and class E addresses. The ranges for different classes of addresses include:
| Class | Address Range | No. of networks | No. of hosts |
|---|---|---|---|
| Class A | 0.0.0.0 to 127.255.255.255 | 128 | 16 million |
| Class B | 128.0.0.0 to 191.255.255.255 | 16,384 | 64000 |
| Class C | 192.0.0.0 to 223.255.255.255 | 2 million | 256 |
| Class D | 224.0.0.0 to 239.255.255.255 | Multicast address | |
| Class E | 240.0.0.0 to 255.255.255.255 | Reserved for future use |
There are different transmission techniques for different receivers and are Unicast, Multicast, Broadcast, and Anycast communication.
- Unicast communication is one-to-one communication. It is a single and direct communication between two devices in an established route.
- Multicast has more than one receiver and only the multicast members receive the multicast traffic. Packets go to a group of computers within the same physical network or a different one, and the packet goes to each member of the multicast network.
- Broadcast communication also has more than one receiver and all receivers get the traffic in the network, despite not being a part of the network.
- Anycast delivers to a group of computers whose addresses have the same prefix. Computers connected to the same physical network share the same prefix addresses.
In anycast communication, the traffic goes to at least one member of the group or the closest or the most easily accessible.
The IP address is a 32-bit address written in dotted decimal notation. The 32-bit address is divided into 4 bytes or 4 octets with 8 bits each. The 4 octets are in the decimal format from numbers 0 to 255. The lowest IP address is 0.0.0.0 and the highest IP address is 255.255.255.255.
What is a Subnet?
The problem that networks faced was that a single class A, B, or C address refers to one network, and not to a collection of LANs. The network providers introduce the subnets to deal with this problem.
A subnet is a logical division of a network. The process of dividing the network into two or more networks creates a subnet. Subnets make networks more efficient as network traffic travels a shorter distance without passing through unnecessary routers to reach its destination. Subnetting simplifies traffic going through a router in charge of a specific network instead of passing through every router to find a specific device.
The class B address can provide up to 64,000 addresses only. Subnetting provides IP addresses as the network grows by splitting the network into several parts for internal use. Yet, it will act as a single network to the outside world.
Each network has its router connected to the main router and when a packet comes into the main router, it routes the packet to the respective subnet. The question is, how will the router find the path to the correct destination?
One way to do this would be to have a table with 64,000 addresses and the router telling the path to take. This idea would work, but it requires a large table in the main router and manual maintenance as hosts are added, moved, or taken out of service.
Instead, a different scheme, the subnet mask, was introduced. The Subnet masks are also written in dotted-decimal notation, with the addition of a slash followed by the number of bits in the network+subnet part. An alternative notation is /22 to indicate that the subnet mask is 22 bits long.
The subnetting is not visible outside the network, so allocating a new subnet does not require contacting the Internet Corporation for Assigned Names and Numbers(ICANN) or changing any external database.
For example, the first subnet might use an IP address starting at 130.50.4.1 and the second subnet might start at 130.50.8.1, and so on.
In the following examples, note the subnets count by fours. The corresponding binary addresses are as follows:
Subnet 1: 10000010 00110010 00000100 00000001
Subnet 2: 10000010 00110010 00001000 00000001
The vertical bar | shows the boundary between the subnet number and the host number. It has a 6-bit subnet number to the left and a 10-bit host number to the right.
How does a Subnet work?
It is important to understand how a router processes IP packets to understand how a subnet works. Each router has a table listing some number of (network,0) IP addresses that tell how to get to the distant networks. The second, (this-network, host) IP address tells how to get to local hosts.
There is a network interface to use to reach the destination associated with each table. When an IP packet arrives, the destination address is looked up in the routing table. If the packet is for a distant network, it gets forward to the next router on the interface given in the table. If it is a local host on the same LAN, then the packet is sent directly to the destination.
The router forwards the packet to a default router with additional information and extensive tables if it cannot find the destination address. This algorithm means that the router must include information about the neighboring networks and their computers in its subnet. It need not worry about all the network and host pairs in the network, which reduces the size of the routing table.
The subnets in the routing tables have entries of the form (this-network, subnet, 0) and (this-network, this-subnet, host). A router on a subnet knows how to get to the hosts on its own subnet.
The router does not need to know the details about the hosts on other subnets because it can find them by executing a Boolean AND function and with the network’s subnet mask instead of storing the IP addresses of hosts of another subnet.
The main router needs a subnet mask to implement subnetting and indicates the split between network+ subnet number and host.
For example, a packet addressed to 130.50.15.6 arriving at the main router is ANDed with the subnet mask 255.255.252.0/22 to give the subnet address 130.50.12.0.
The router searches for this address in the routing tables to find out which output line to use to get to that router. Subnetting reduces router table space by creating a three-level hierarchy consisting of network, subnet, and host.
What is a Subnet Mask?
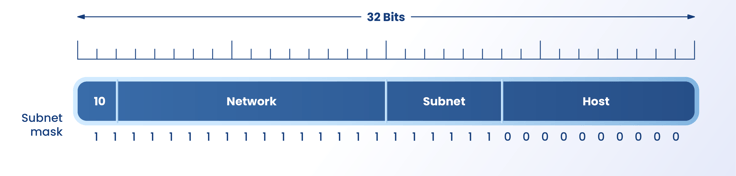
An IP address has two components, the network address, and the host address. A subnet mask separates the IP address into the network and a host address (<network><host>). Subnetting further divides the host part of an IP address into a subnet and host address (<network><subnet><host>). It is called a subnet mask because it helps identify the network address of an IP address by performing a bitwise AND operation on the netmask.
A subnet mask is a 32-bit number that masks an IP address and divides the IP address into network address and host address. Setting the network bits to all 1’s and setting the host bits to all 0’s creates the subnet mask. Within a network, the router reserves two host addresses for a special purpose. The router assigns all 0’s address to a network address and all 255’s to a broadcast address, but never to a host.
| Class | Total no. of hosts | Netmask(Binary) | Netmask(Decimal) |
|---|---|---|---|
| A | 16,777,216 | 11111111 11111111 11111111 00000000 | 255.255.255.0 |
| B | 65,534 | 11111111 11111111 00000000 00000000 | 255.255.0.0 |
| C | 256 | 11111111 00000000 00000000 00000000 | 255.0.0.0 |
Applying a subnet mask to an IP address separates the network address from the host address. The 1’s represent the network bits in the mask, and the 0’s represent the host bits. Performing a bitwise logical AND operation on the IP address with the subnet mask produces the network address.
How does a Subnet Mask work?
A mask is a 32-bit binary number that gives the first address in the block when bitwise ANDed with an address in the block. When there are subnets, an address uses a mask to extract the network address from the destination address.
For example,
For the IP address 216.003.218.12, the dotted-decimal format is – 11011000.00000011.10000000.00001100
It belongs to the class C address, therefore the mask is 255.255.255.000.
The dotted decimal format is 11111111.11111111.11111111 .00000000.
Therefore, the network address is
216.003.218.0 – 11011000.00000011.10000000. 00000000.
The first 24 bits are the network address, and the last 8 bits (the remaining zeros in the subnet mask) are the host address. This gives you the following:
11011000.00000011.10000000. 00000000– Network address (216.003.218.0)
00000000.00000000.00000000.00001100 — Host address (000.000.000.12)
Final Thoughts
The internet is growing exponentially and it is imperative to understand how IP addresses work and why networks use subnetting. Subnetting divides a large network into a smaller network for avoiding congestion, traffic management, and better management of the network.
ProxyScrape offers proxies for various applications and it operates over the internet. There are flexible plans for you to choose proxies for scraping websites. Keep visiting our blogs to learn more about proxies and their various applications.