What is a Proxy Firewall and How Does It Work
Proxy firewalls can be considered network security systems that filter messages at the application layer. They are also called gateway or application firewalls that limit the applications a network can support. Though they increase the security levels, they affect the speed and functionality. The traditional firewall can neither inspect application protocol traffic nor decrypt traffic.
Table of Contents
- Working of A Proxy Firewall
- Advantages of a Proxy Firewall Control and granularityThreat assessmentLogging capabilitiesSecurity
- Control and granularity
- Threat assessment
- Logging capabilities
- Security
- Disadvantages of a Proxy Firewall Slow PerformanceChallenging to UseCost of a Proxy ServerDifficulty in Configurations
- Slow Performance
- Challenging to Use
- Cost of a Proxy Server
- Difficulty in Configurations
- How Are Proxy Firewalls Used?
- Conclusion
Proxy firewalls can be considered network security systems that filter messages at the application layer. They are also called gateway or application firewalls that limit the applications a network can support. Though they increase the security levels, they affect the speed and functionality.
The traditional firewall can neither inspect application protocol traffic nor decrypt traffic. It typically uses an antivirus solution or an intrusion prevention system (IPS) for protecting against threats. Proxy servers fill the gap and act as an intermediary between the servers and computers on the Internet. They secure data that go in and out of a network. They analyze the incoming traffic and detect the signs of malware or a potential cyberattack. Proxy server firewalls filter, cache, and control requests from devices for keeping networks secure and preventing access to cyberattacks or unauthorized parties.
Working of A Proxy Firewall
You can consider a proxy firewall the most secure form of firewall because it does not allow networks to contact each other directly. Also, it has its own IP address, so the external network connection can not receive packets from the network directly.
Proxy firewalls enable organizations to access the threat level of application protocols and implement error detection, validity checks, and attack detection. They use proxy-based architecture and tactics like deep packet inspection (DPI) for discovering advanced threats and analyzing application traffic.
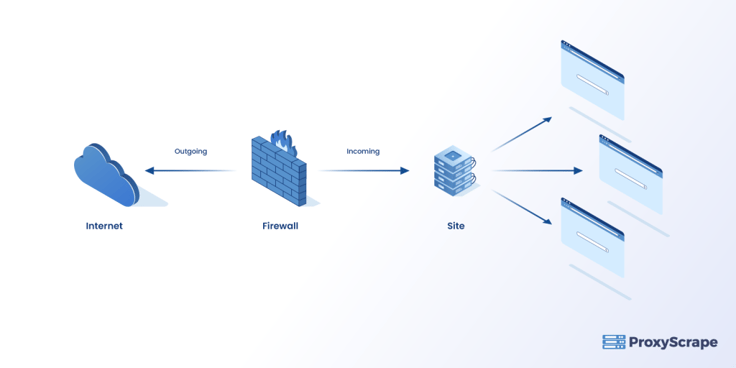
Any user who attempts to access an external site through a proxy firewall must follow the below steps.
- The user uses a protocol such as Hypertext Transfer Protocol (HTTP) and File Transfer Protocol (FTP) to request access to the Internet.
- The user’s computer sends a synchronized (SYN) message from its IP address to the server’s IP address, thus creating a session between itself and the server.
- The proxy firewall picks off the request and replies with the SYN-ACK (synchronize-acknowledge) message packet from its IP address to the server’s IP address.
- When the user computer receives the SYN-ACK packet, it sends a final ACK (acknowledge) packet to the server’s IP address. It ensures a connection to the proxy but not a valid TCP (Transmission Control Protocol) connection.
- The proxy sends an SYN packet from its IP address and completes the connection to the external server. When the server receives the SYN-ACK packet, it responds with an ACK packet. This ensures a valid TCP connection between the user’s computer and the proxy and between the proxy and the external server.
Advantages of a Proxy Firewall
Given below are the advantages of a proxy firewall.
Control and granularity
The significant benefit of a proxy firewall is that it offers more granularity and control than other types of firewalls. It is because it can contain access logs for detailed reports on user activities and can be configured for applying security levels to individual users and groups.
Threat assessment
Proxy firewalls are an easier way for programmers to:
- Deploy error and attack detection
- Assess the threat levels of application protocols
- Validity checking
Logging capabilities
Proxy firewalls can not only examine the network access and the port number, but they can also analyze the entire network packet. The logging capabilities of the proxy firewall acts as a valuable resource for security administrators when they have to deal with security incidents.
Security
Proxy firewalls prevent direct network contact with other systems and are considered the most secure firewall type. You know that the proxy firewall has its own IP address, so it does not allow the external network connections to receive the network packets directly.
Disadvantages of a Proxy Firewall
Given below are the disadvantages of a proxy firewall.
Slow Performance
A proxy firewall can slow down the internet connection. It is because it acts as a third party between the user computer and the Internet and establishes an additional link for the incoming and the outgoing packets. Consequently, the proxy firewall can slow down the performance and become a single point of failure, thus acting as a bottleneck.
Challenging to Use
The main disadvantage of proxy firewalls is that they are challenging to use. Many users become frustrated and disable them when they use applications that can not access the Internet.
Cost of a Proxy Server
The operation and deployment of a proxy server can be expensive. Small enterprises can not handle the cost of setting up a proxy server. Further, aside from the setup cost, there are several other costs to consider.
Difficulty in Configurations
The proxy setups are pre-programmed for achieving a specific objective. Therefore, some processing needs to be done to meet other sets of requirements. It might be a challenging task to set up a proxy. You have to construct it in a way such that the hackers can not access your confidential material.
How Are Proxy Firewalls Used?
You can use proxy firewalls to protect critical systems from unauthorized access as they act as a barrier between authorized and unauthorized users. You can deploy a proxy firewall within a hardware device such as a firewall or a router. Proxy firewalls can help you accomplish the following things.
- Protection against espionage and network intrusion
- Ensuring that only authorized users have access to the resources of a computer network
- Filtering out unwanted packets and messages on an internet network
Proxy firewalls can also be used to restrict access to sensitive sites and the sites relevant to specific users. For instance, you can use a proxy firewall to prevent employees from accessing Twitter or Facebook during working hours.
Conclusion
So far, we discussed that a proxy firewall filters messages at the application layer and protects the network resources. It acts as a gateway between the public Internet and the secure local network. The internal network devices first interact with the proxy gateway to access the Internet. Proxy firewalls also offer system security by limiting the content entering and exiting the system. They monitor, inspect and manage requests originating from a user to maintain the network free and safe from malware and attackers. Some significant benefits of using a proxy firewall are as:
- It ensures anonymity.
- It protects a user’s computer from security threats.
- It can unblock a restricted website.